Hacking tools: C99 Shell

What is a web shell?
A web shell is a script that is often uploaded to a server with the aim of giving a hacker the remote control of a machine. Web servers that become infected can either be internal to the network or internet-facing, where the shell is utilized to pivot further to the server’s internal hosts (Alert (TA15-314A)).
A hacker can use any language to write the web shell as long as it is supported by the target web server. Some of the most common web shells are in languages that are broadly supported, for example, PHP. A hacker can pinpoint weaknesses that he or she can exploit and install a type of web shell utilizing network scouting tools. For instance, these vulnerabilities occur in web server software or CMS’s or content management systems. Once they have been uploaded successfully, a hacker can then use the shells to leverage other techniques of exploitation to issue commands and escalate privileges remotely. The controls are connected to the functionality or opportunity available to the server directly and may include the capacity to delete, add and execute files, in addition, to the ability to operate further executables, commands or scripts (Alert (TA15-314A)).
Web shells can also be used deliberately and legitimately by an administrator of a system to carry out actions on the server, for example, reading system logs, creating a user and restarting a service. Unlike some other types of shells like reverse shells that need a secondary program to operate on the machine of a victim, a web shell needs no sockets for communication and are often run over HTTP (Paganini, 2016).
They are backdoors that operate from the browser. As such, they are considered tools for exploitation. Before they can be utilized to victimize a user, a weakness has to be found on the target application. An excellent way that hackers do this is by uploading the threat through a page for file upload, for instance, a submission form on an organization’s website and then utilizing LFI or Local File Include vulnerability in the app to include the shell in its pages (Paganini, 2016).
The c99 web shell
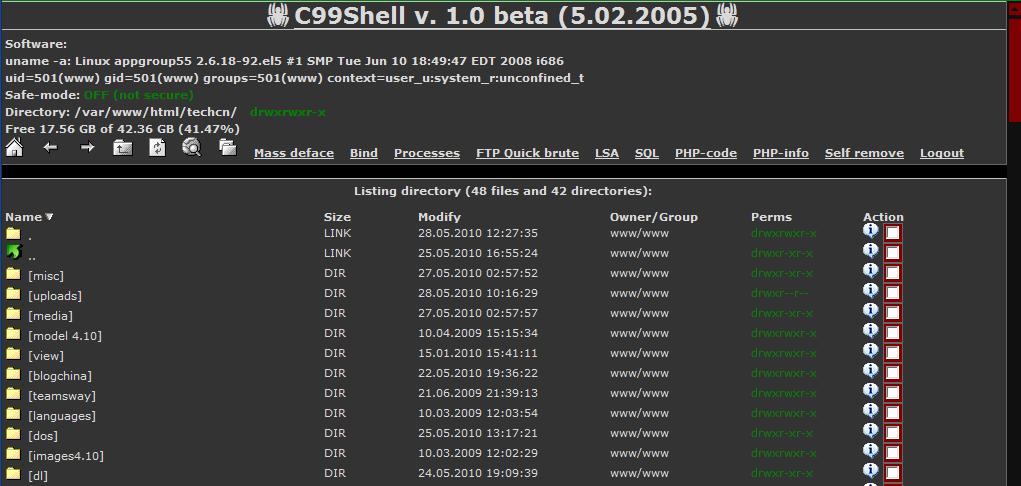
An excellent example of a web shell is the c99 variant, which is a PHP malware often uploaded to a vulnerable web application to give hackers an interface. The c99 shell lets the attacker take control of the processes of the Internet server, allowing him or her give commands on the server as the account under which the threat is operating. It lets the hacker upload, browse the file system, edit and view files, in addition, to deleting, moving them and changing permissions. Finding a c99 shell is an excellent way to identify a compromise on a system. The c99 shell is about 1500 lines long, and some of its traits include showing security measures the web server may use, a file viewer that has permissions, a place where the attacker can operate custom PHP code (PHP malware c99 shell).
There are different variants of the c99 shell that are being used today. Below is an example of a relatively recent one. It has many signatures that can be utilized to write protective countermeasures.
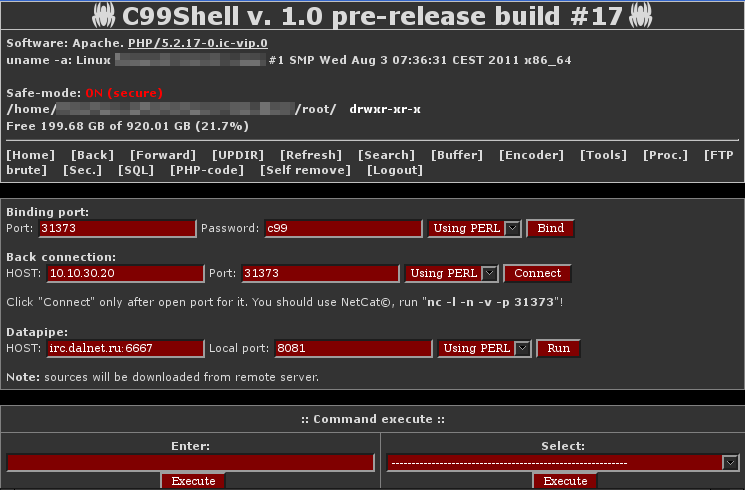
The c99 shell type used in most attacks can be detected by a significant number of antivirus software.
Experts also can identify it by its common file name and URL, pagat.txt. Its file includes a PHP script that has been disguised. This way, the attackers hide a malicious code that they use to bypass the WAF or web application firewall that often protects the site. When the script has been written on the target server, the attacker often receives an email notifying him or her of the compromise. The image below shows a GET request that has been seen in the c99 attacks (Paganini, 2016).
References
Alert (TA15-314A). Compromised web servers and web shells- Threat awareness and guidance. US- CERT. Retrieved from https://www.us-cert.gov/ncas/alerts/TA15-314A
Paganini, P (2016). IBM warns a spike in the number of PHP C99 web shell attacks. Retrieved from http://securityaffairs.co/wordpress/46449/hacking/c99-webshell-attacks.html